程序分析
2024-12-9
容器密码
mW7@B!tRp*Xz46Y9#KFUV^J2&NqoHqTpLCE%8rvGW(AX#1k@YL3$M5!bWY*9HLFq7UZR6^T!XoVmPK28J&CY9%6(Arz#tbU4oXYKLp7Wq^FV9H
检材:通过网盘分享的文件:团队赛检材容器 链接: https://pan.baidu.com/s/1GjitvFChM3VmOzKA1Gz46Q?pwd=znck 提取码: znck
当时去公网机传了一下微步。
提示:请勿在真机上运行或分析该exe
1. 通过分析恶意程序,找出运行该软件必要的参数是?(答案格式:--xxx-xxx) (2.0分)
--access-token
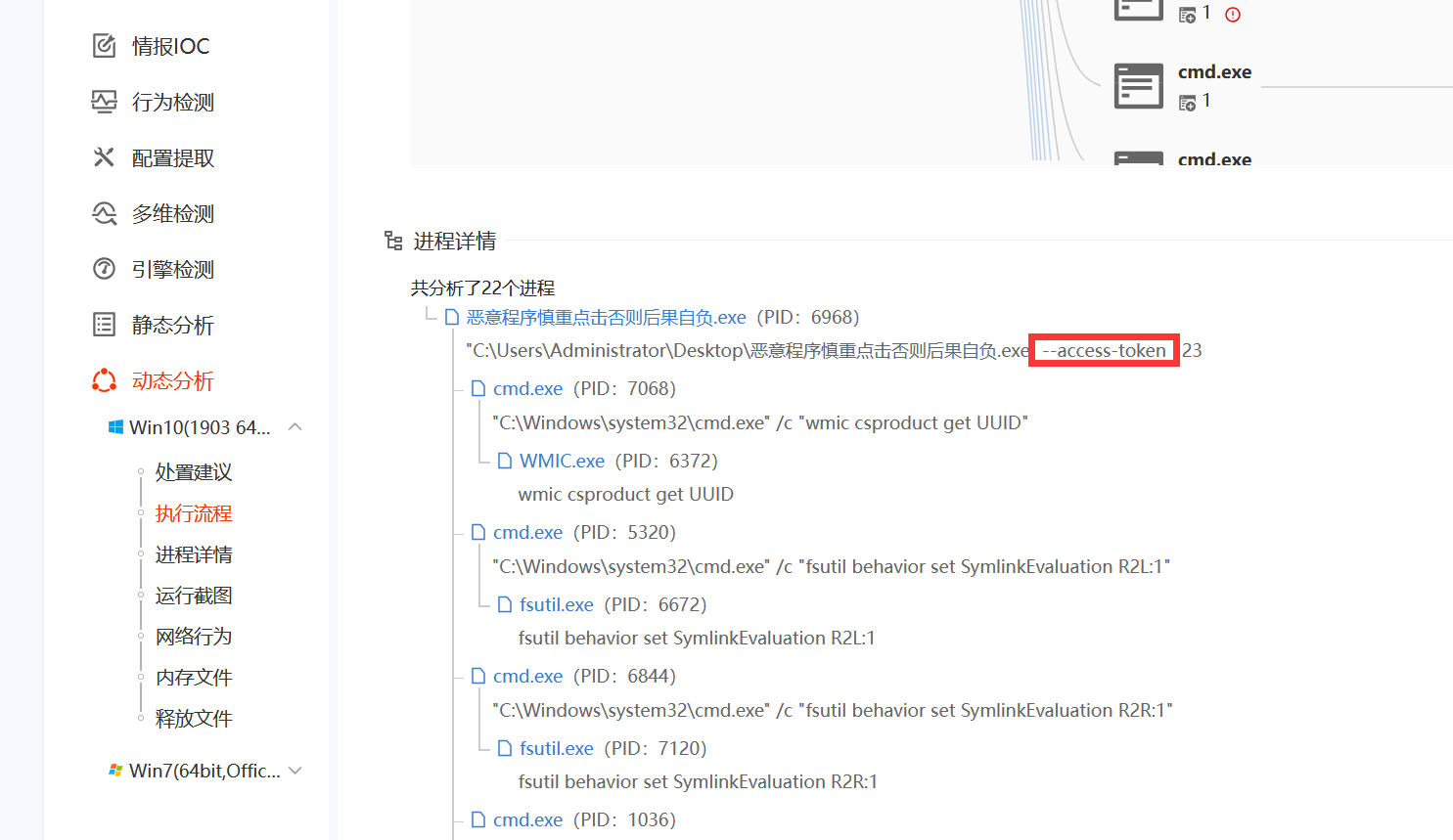
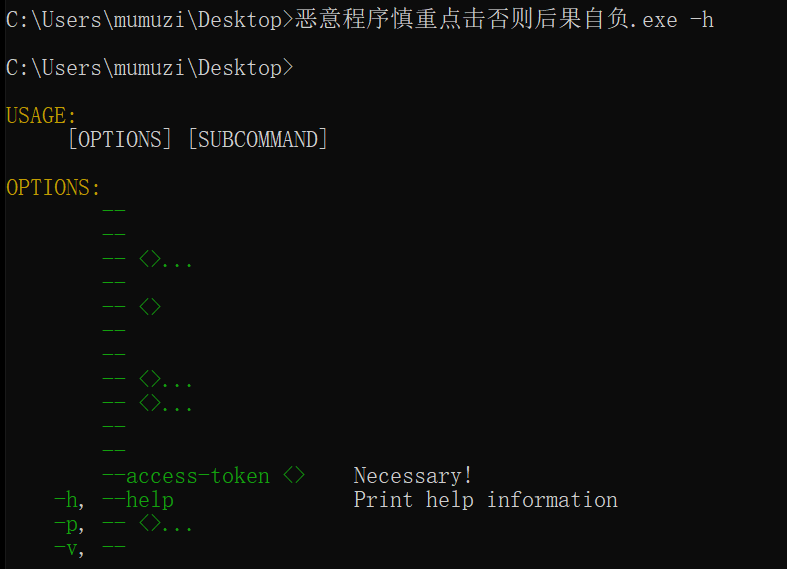
实际上带参数 -h也能看见
2. 该程序为了控制控制最大并发数,在注册表中设置了MaxMpxCt参数,请给出设置参数的具体值。(答案格式:纯数字) (2.0分)
65533
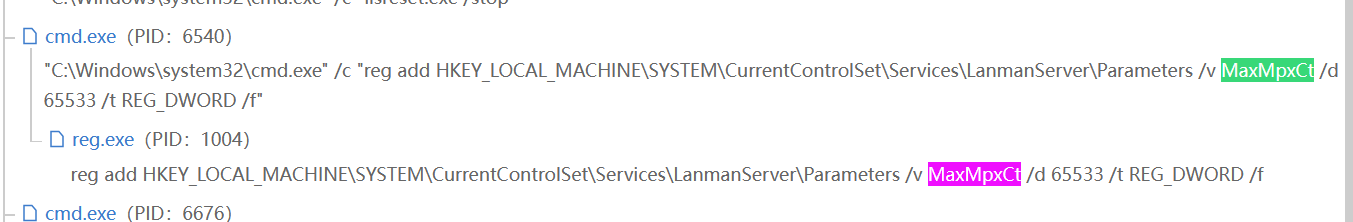
实际上IDA里面也能看见,搜字符串即可
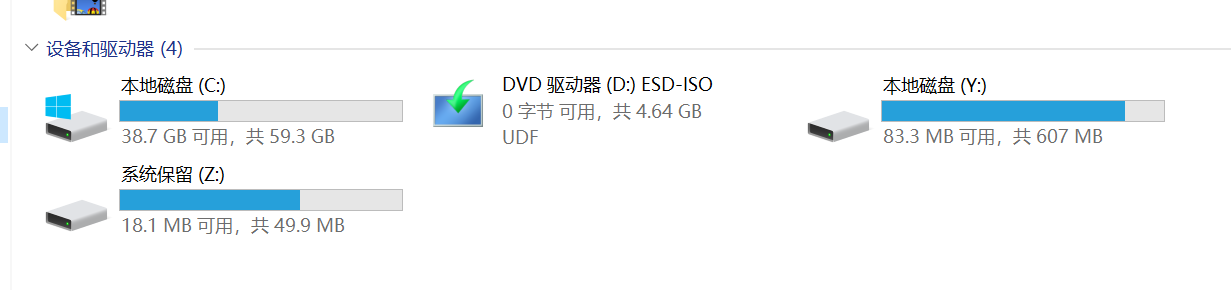
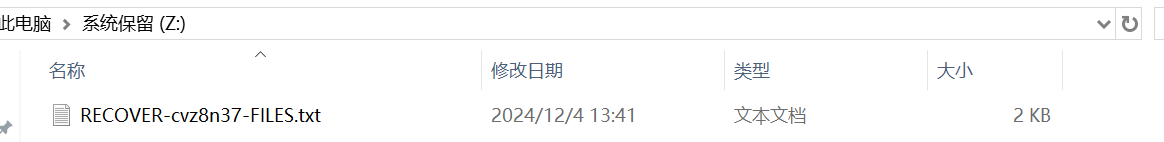
3. 该程序运行过程中会创建新的分区磁盘,请写出该分区磁盘一级目录中的文件名。(答案格式:如有字母请大写) (2.0分)
RECOVER-cvz8n37-FILES.txt
运行程序,恶意程序慎重点击否则后果自负.exe --access-token 123
4. 该程序获取计算机名时使用的kernel32库函数是什么?(答案格式:kernel32.xxx) (2.0分)
kernel32.GetComputerNameW
先搜字符串,然后定位一下交叉引用
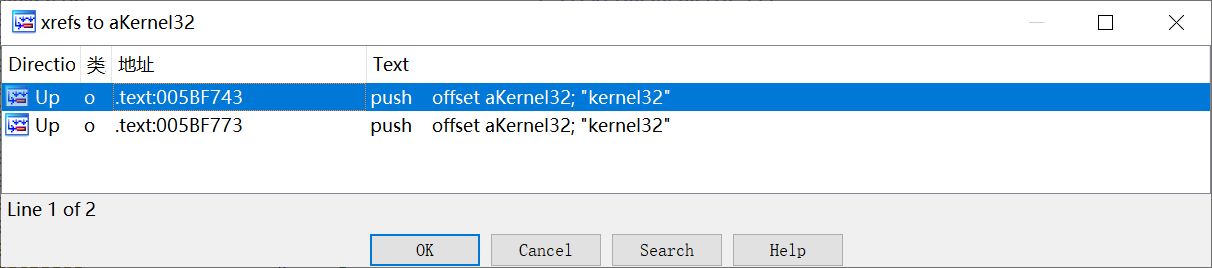
然后只发现这两个
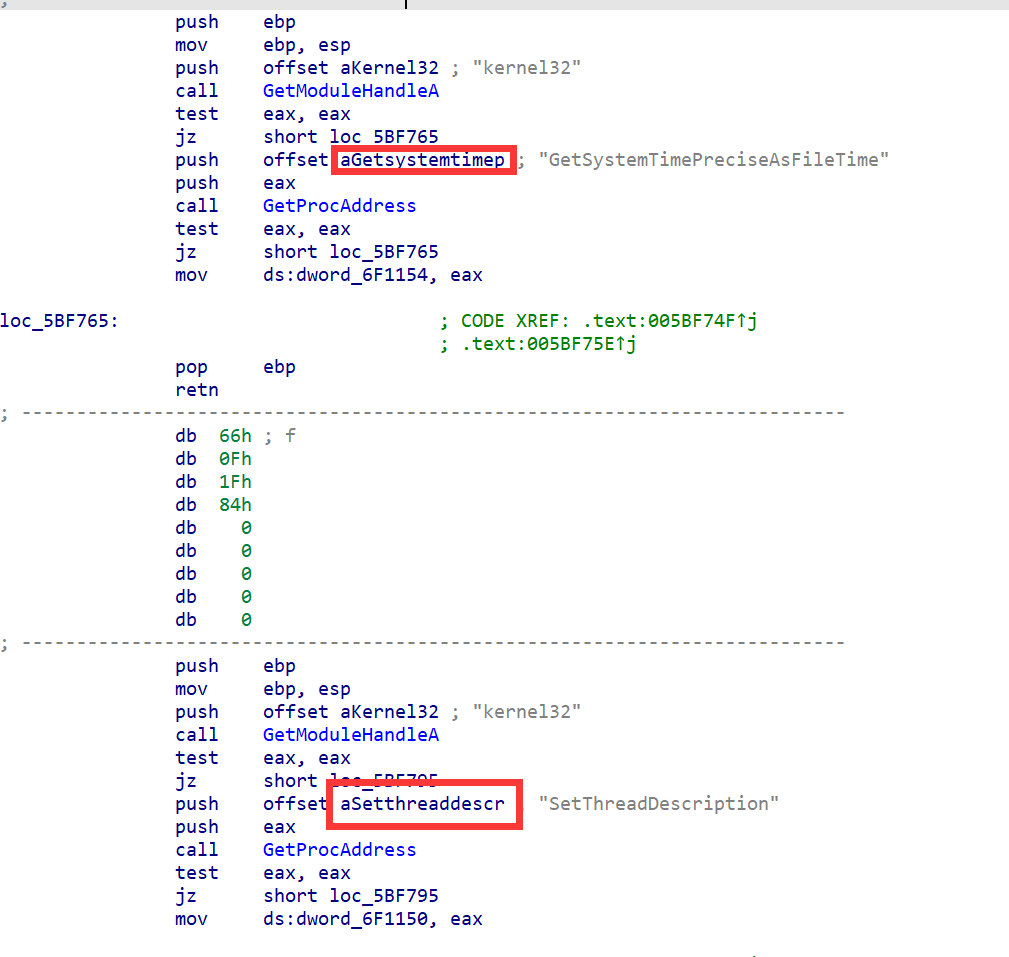
那么搜 Name,发现有个computer_name
跳过来看看交叉引用,然后回到函数
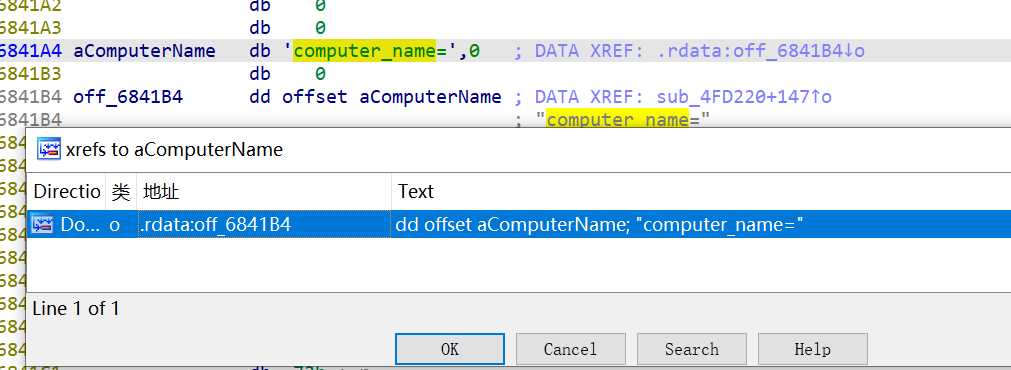
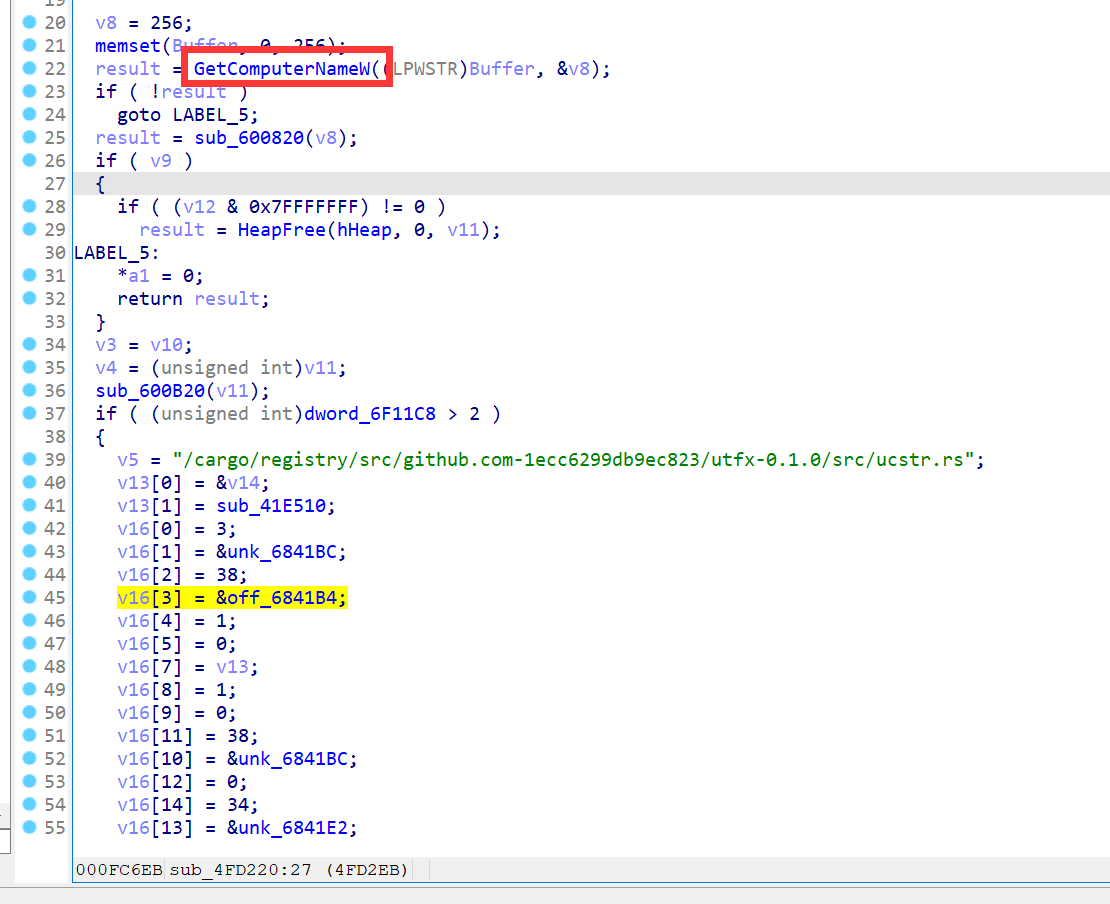
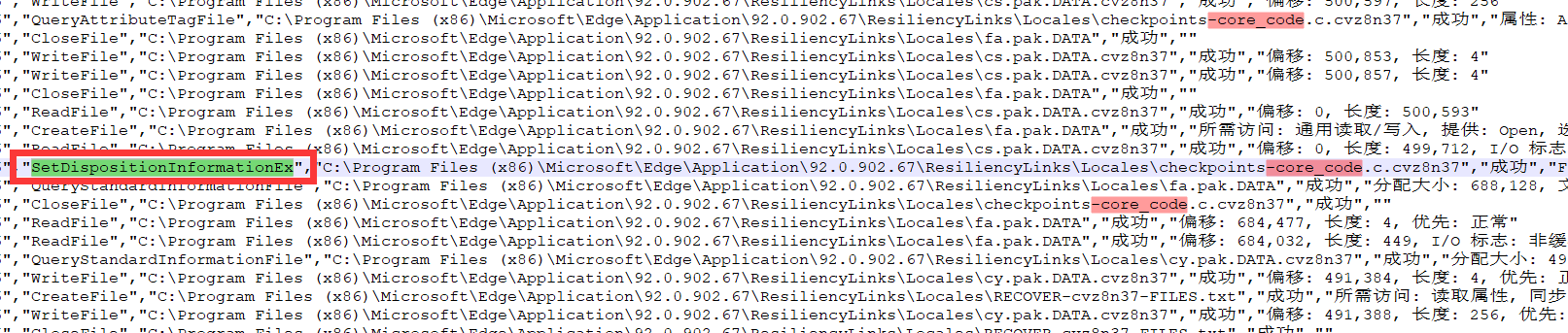
5. 根据该程序的加密过程逻辑,已知加密文件后缀为cvz8n37,且系统中存在core_code.c文件,请写出程序在加密该文件前生成的文件名。(答案格式:xxx.cvz8n37) (3.0分)
checkpoints-core_code.c.cvz8n37
创建一个core_code.c,并且在里面写上任意内容。用Process Monitor抓取之后导出所有与该恶意程序有关的到csv表格中
首先查看一下core_code.c被加密�后的文件名,发现在加密后的文件名是core_code.c.cvz8n37
那么就需要找一下和这个文件有关的
首先是读取当前目录下的文件有哪些

接着后面是读取了文件内容,并且创了个新文件(也是最终文件)
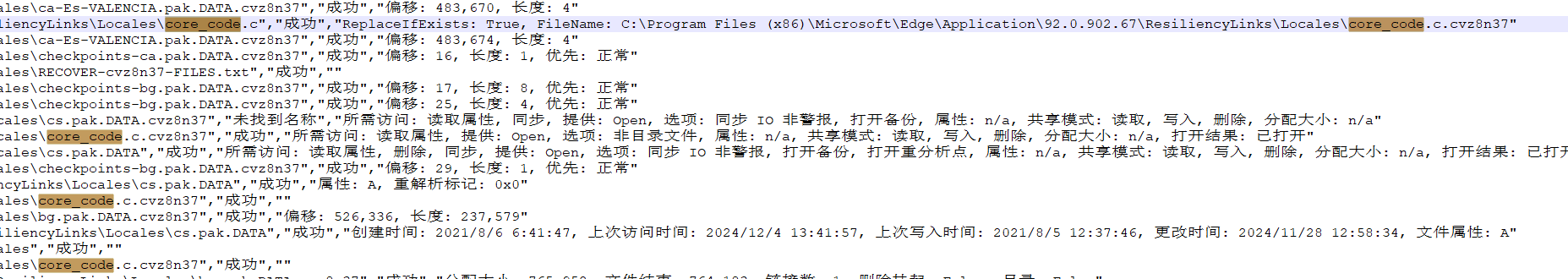
然后创建了一个临时文件
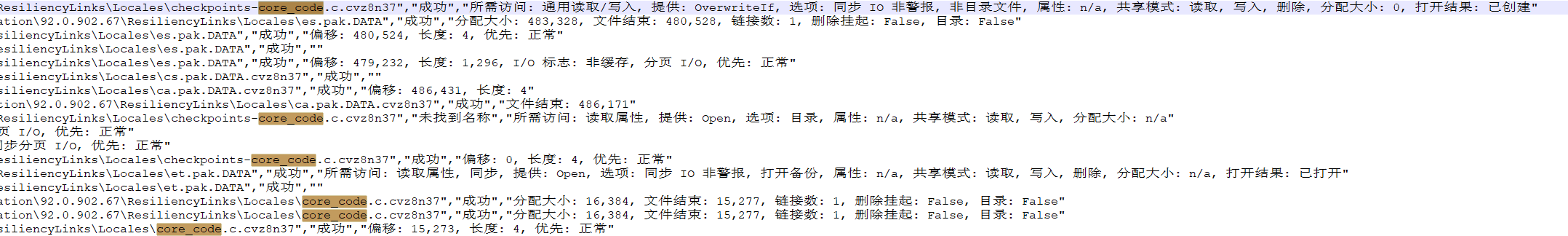
将文件内容写入临时后又copy到最终文件,然后删除了这个临时文件
6. 该程序在提权过程中会申请多项Windows权限,请写出尝试申请的第三项权限名。(答案格式:答案格式需与实际一致) (4.0分)
SeLoadDriverPrivilege
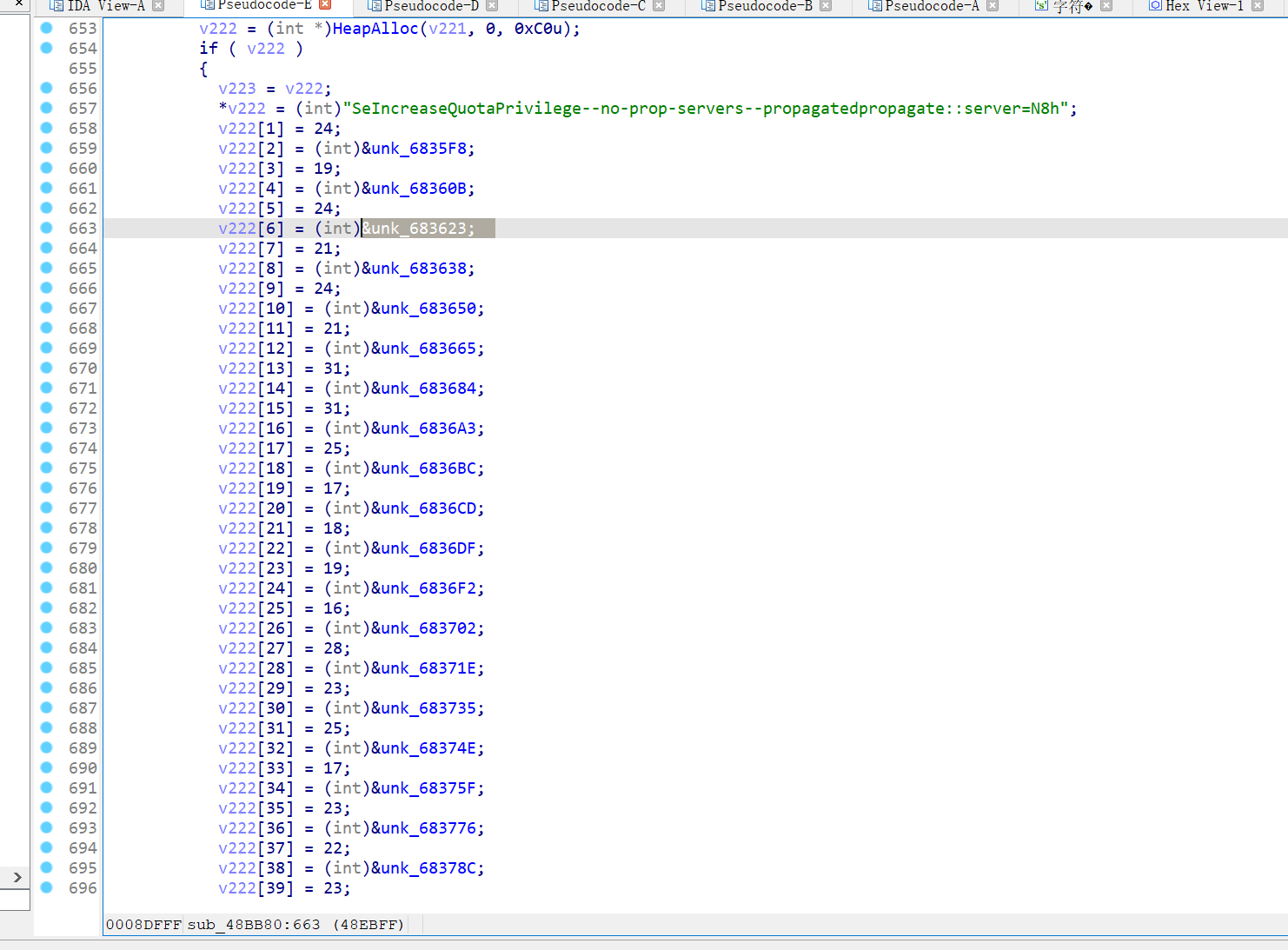
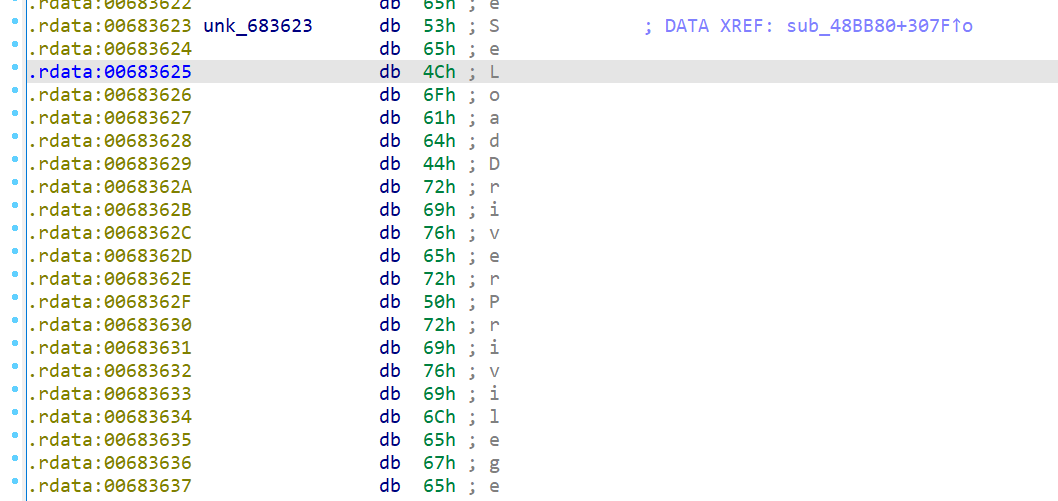
第三个unk_683623
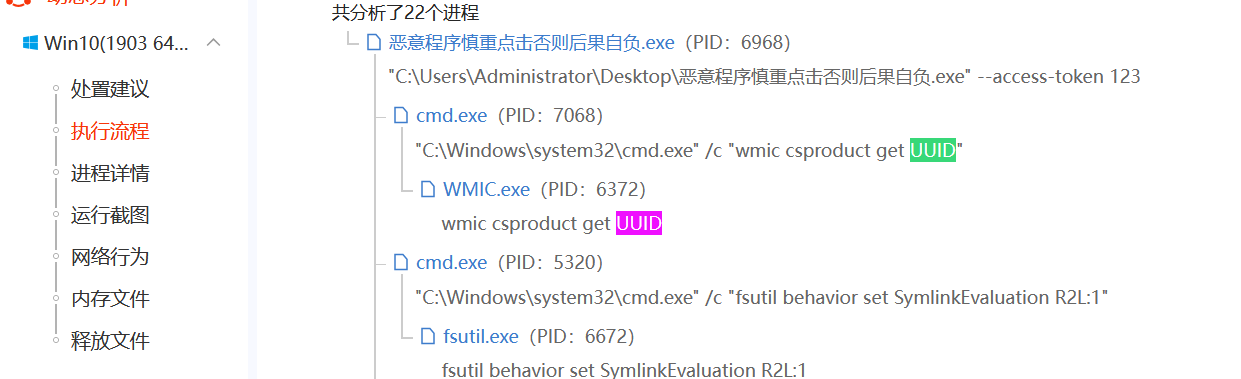
7. 该程序运行过程中获取UUID时的完整命令为?(答案格式:"D:\xxx...\xxx.exe" xx "xxx xxx xxx xxx" (4.0分)
"C:\Windows\system32\cmd.exe" /c "wmic csproduct get UUID"
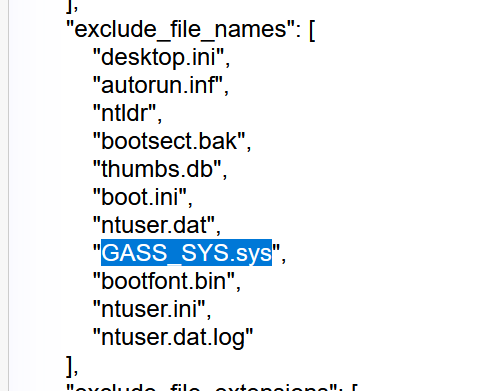
8. 该程序存在着默认配置文件,在该配置文件中默认不加密且文件后缀为sys的文件名是?(答案格式:包含后缀名,如xxxx.sys) (4.0分)
GASS_SYS.sys
在IDA中搜索一下config
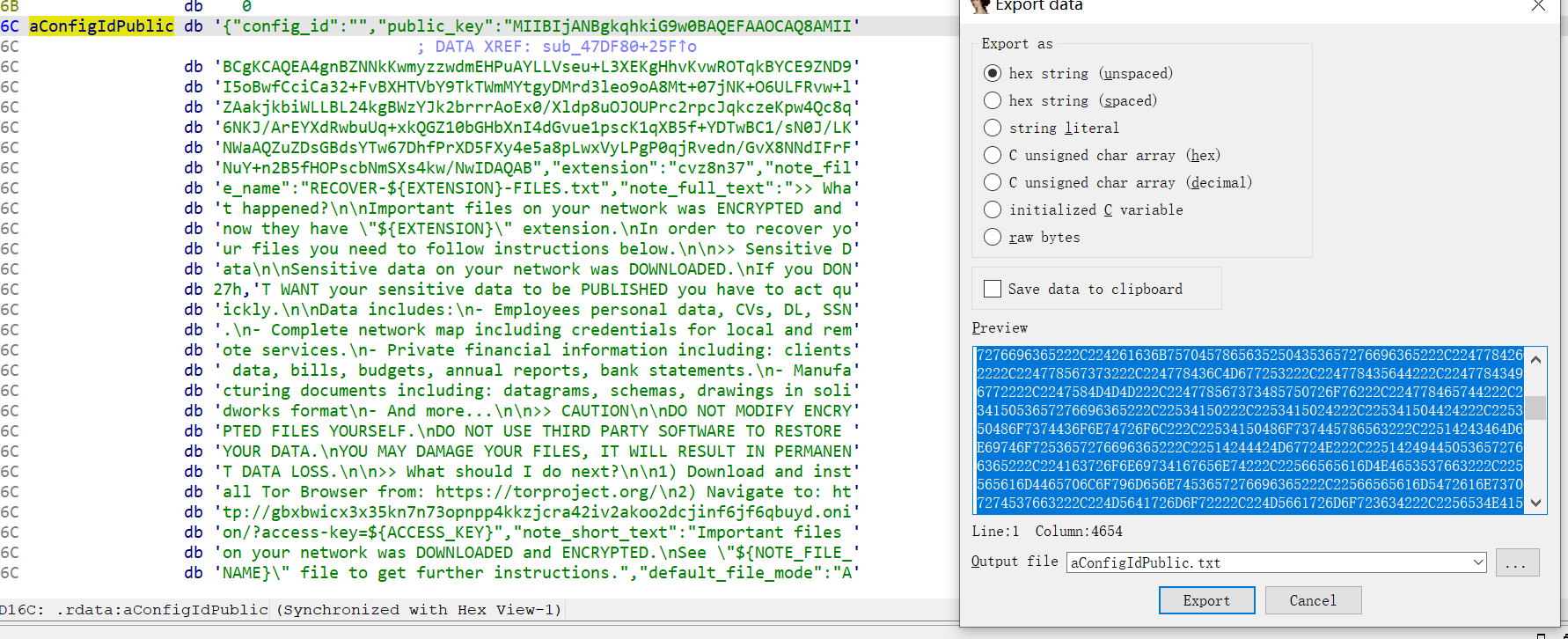
找到,然后导出,格式化一下json
{
"config_id": "",
"public_key": "MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA4gnBZNNkKwmyzzwdmEHPuAYLLVseu+L3XEKgHhvKvwROTqkBYCE9ZND9I5oBwfCciCa32+FvBXHTVbY9TkTWmMYtgyDMrd3leo9oA8Mt+07jNK+O6ULFRvw+lZAakjkbiWLLBL24kgBWzYJk2brrrAoEx0/Xldp8uOJOUPrc2rpcJqkczeKpw4Qc8q6NKJ/ArEYXdRwbuUq+xkQGZ10bGHbXnI4dGvue1pscK1qXB5f+YDTwBC1/sN0J/LKNWaAQZuZDsGBdsYTw67DhfPrXD5FXy4e5a8pLwxVyLPgP0qjRvedn/GvX8NNdIFrFNuY+n2B5fHOPscbNmSXs4kw/NwIDAQAB",
"extension": "cvz8n37",
"note_file_name": "RECOVER-${EXTENSION}-FILES.txt",
"note_full_text": ">> What happened?\n\nImportant files on your network was ENCRYPTED and now they have \"${EXTENSION}\" extension.\nIn order to recover your files you need to follow instructions below.\n\n>> Sensitive Data\n\nSensitive data on your network was DOWNLOADED.\nIf you DON'T WANT your sensitive data to be PUBLISHED you have to act quickly.\n\nData includes:\n- Employees personal data, CVs, DL, SSN.\n- Complete network map including credentials for local and remote services.\n- Private financial information including: clients data, bills, budgets, annual reports, bank statements.\n- Manufacturing documents including: datagrams, schemas, drawings in solidworks format\n- And more...\n\n>> CAUTION\n\nDO NOT MODIFY ENCRYPTED FILES YOURSELF.\nDO NOT USE THIRD PARTY SOFTWARE TO RESTORE YOUR DATA.\nYOU MAY DAMAGE YOUR FILES, IT WILL RESULT IN PERMANENT DATA LOSS.\n\n>> What should I do next?\n\n1) Download and install Tor Browser from: https://torproject.org/\n2) Navigate to: http://gbxbwicx3x35kn7n73opnpp4kkzjcra42iv2akoo2dcjinf6jf6qbuyd.onion/?access-key=${ACCESS_KEY}",
"note_short_text": "Important files on your network was DOWNLOADED and ENCRYPTED.\nSee \"${NOTE_FILE_NAME}\" file to get further instructions.",
"default_file_mode": "Auto",
"default_file_cipher": "Best",
"credentials": [
],
"kill_services": [
"mepocs",
"memtas",
"veeam",
"svc$",
"backup",
"sql",
"vss",
"msexchange",
"sql$",
"mysql",
"mysql$",
"sophos",
"MSExchange",
"MSExchange$",
"WSBExchange",
"PDVFSService",
"BackupExecVSSProvider",
"BackupExecAgentAccelerator",
"BackupExecAgentBrowser",
"BackupExecDiveciMediaService",
"BackupExecJobEngine",
"BackupExecManagementService",
"BackupExecRPCService",
"GxBlr",
"GxVss",
"GxClMgrS",
"GxCVD",
"GxCIMgr",
"GXMMM",
"GxVssHWProv",
"GxFWD",
"SAPService",
"SAP",
"SAP$",
"SAPD$",
"SAPHostControl",
"SAPHostExec",
"QBCFMonitorService",
"QBDBMgrN",
"QBIDPService",
"AcronisAgent",
"VeeamNFSSvc",
"VeeamDeploymentService",
"VeeamTransportSvc",
"MVArmor",
"MVarmor64",
"VSNAPVSS",
"AcrSch2Svc"
],
"kill_processes": [
"agntsvc",
"dbeng50",
"dbsnmp",
"encsvc",
"excel",
"firefox",
"infopath",
"isqlplussvc",
"msaccess",
"mspub",
"mydesktopqos",
"mydesktopservice",
"notepad",
"ocautoupds",
"ocomm",
"ocssd",
"onenote",
"oracle",
"outlook",
"powerpnt",
"sqbcoreservice",
"sql",
"steam",
"synctime",
"tbirdconfig",
"thebat",
"thunderbird",
"visio",
"winword",
"wordpad",
"xfssvccon",
"*sql*",
"bedbh",
"vxmon",
"benetns",
"bengien",
"pvlsvr",
"beserver",
"raw_agent_svc",
"vsnapvss",
"CagService",
"QBIDPService",
"QBDBMgrN",
"QBCFMonitorService",
"SAP",
"TeamViewer_Service",
"TeamViewer",
"tv_w32",
"tv_x64",
"CVMountd",
"cvd",
"cvfwd",
"CVODS",
"saphostexec",
"saposcol",
"sapstartsrv",
"avagent",
"avscc",
"DellSystemDetect",
"EnterpriseClient",
"VeeamNFSSvc",
"VeeamTransportSvc",
"VeeamDeploymentSvc"
],
"exclude_directory_names": [
"system volume information",
"intel",
"$windows.~ws",
"application data",
"$recycle.bin",
"mozilla",
"$windows.~bt",
"public",
"msocache",
"windows",
"default",
"all users",
"tor browser",
"programdata",
"boot",
"config.msi",
"google",
"perflogs",
"appdata",
"windows.old"
],
"exclude_file_names": [
"desktop.ini",
"autorun.inf",
"ntldr",
"bootsect.bak",
"thumbs.db",
"boot.ini",
"ntuser.dat",
"GASS_SYS.sys",
"bootfont.bin",
"ntuser.ini",
"ntuser.dat.log"
],
"exclude_file_extensions": [
"themepack",
"nls",
"diagpkg",
"msi",
"lnk",
"exe",
"cab",
"scr",
"bat",
"drv",
"rtp",
"msp",
"prf",
"msc",
"ico",
"key",
"ocx",
"diagcab",
"diagcfg",
"pdb",
"wpx",
"hlp",
"icns",
"rom",
"dll",
"msstyles",
"mod",
"ps1",
"ics",
"hta",
"bin",
"cmd",
"ani",
"386",
"lock",
"cur",
"idx",
"sys",
"com",
"deskthemepack",
"shs",
"ldf",
"theme",
"mpa",
"nomedia",
"spl",
"cpl",
"adv",
"icl",
"msu"
],
"exclude_file_path_wildcard": [
],
"enable_network_discovery": true,
"enable_self_propagation": true,
"enable_set_wallpaper": true,
"enable_esxi_vm_kill": true,
"enable_esxi_vm_snapshot_kill": true,
"strict_include_paths": [
],
"esxi_vm_kill_exclude": [
]
}
*9. 请写出该程序加密文件过程中,生成私钥函数返回值内"chipher"键对应的值。 (6.0分)
需要动调