WKCTF2024
DK盾云服务器
 最近群里有抽奖活动,可以加群看看
最近群里有抽奖活动,可以加群看看

Misc
signin
不是10点开赛吗?9点40看了一眼才发现改成9点了,有�点幽默细胞。
一眼就是twin-hex
https://www.calcresult.com/misc/cyphers/twin-hex.html
解出来是个png图片

不套是你的谎言
一眼没想出来是啥,搜了前两个之后发现是pyc magic number,找到这个
https://simryang.tistory.com/entry/python-magic-number
然后发现magic.txt的都在这上面,因此写个脚本,发现全是python3,猜测是后面的版本号,组合起来之后不是tupper,尝试n2s得到了一个zip,代码如下
magic_number_versions = {
0x02099900: "python 1.0 byte-compiled",
0x03099900: "python 1.1/1.2 byte-compiled",
0x892e0d0a: "python 1.3 byte-compiled",
0x04170d0a: "python 1.4 byte-compiled",
0x994e0d0a: "python 1.5 byte-compiled",
0xfcc40d0a: "python 1.6 byte-compiled",
0xfdc40d0a: "python 1.6 byte-compiled",
0x87c60d0a: "python 2.0 byte-compiled",
0x88c60d0a: "python 2.0 byte-compiled",
0x2aeb0d0a: "python 2.1 byte-compiled",
0x2beb0d0a: "python 2.1 byte-compiled",
0x2ded0d0a: "python 2.2 byte-compiled",
0x2eed0d0a: "python 2.2 byte-compiled",
0x3bf20d0a: "python 2.3 byte-compiled",
0x3cf20d0a: "python 2.3 byte-compiled",
0x45f20d0a: "python 2.3 byte-compiled",
0x59f20d0a: "python 2.4 byte-compiled",
0x63f20d0a: "python 2.4 byte-compiled",
0x6df20d0a: "python 2.4 byte-compiled",
0x6ef20d0a: "python 2.4 byte-compiled",
0x77f20d0a: "python 2.5 byte-compiled",
0x81f20d0a: "python 2.5 byte-compiled",
0x8bf20d0a: "python 2.5 byte-compiled",
0x8cf20d0a: "python 2.5 byte-compiled",
0x95f20d0a: "python 2.5 byte-compiled",
0x9ff20d0a: "python 2.5 byte-compiled",
0xa9f20d0a: "python 2.5 byte-compiled",
0xb3f20d0a: "python 2.5 byte-compiled",
0xb4f20d0a: "python 2.5 byte-compiled",
0xc7f20d0a: "python 2.6 byte-compiled",
0xd1f20d0a: "python 2.6 byte-compiled",
0xd2f20d0a: "python 2.6 byte-compiled",
0xdbf20d0a: "python 2.7 byte-compiled",
0xe5f20d0a: "python 2.7 byte-compiled",
0xeff20d0a: "python 2.7 byte-compiled",
0xf9f20d0a: "python 2.7 byte-compiled",
0x03f30d0a: "python 2.7 byte-compiled",
0x04f30d0a: "python 2.7 byte-compiled",
0xb80b0d0a: "python 3.0 byte-compiled",
0xc20b0d0a: "python 3.0 byte-compiled",
0xcc0b0d0a: "python 3.0 byte-compiled",
0xd60b0d0a: "python 3.0 byte-compiled",
0xe00b0d0a: "python 3.0 byte-compiled",
0xea0b0d0a: "python 3.0 byte-compiled",
0xf40b0d0a: "python 3.0 byte-compiled",
0xf50b0d0a: "python 3.0 byte-compiled",
0xff0b0d0a: "python 3.0 byte-compiled",
0x090c0d0a: "python 3.0 byte-compiled",
0x130c0d0a: "python 3.0 byte-compiled",
0x1d0c0d0a: "python 3.0 byte-compiled",
0x1f0c0d0a: "python 3.0 byte-compiled",
0x270c0d0a: "python 3.0 byte-compiled",
0x3b0c0d0a: "python 3.0 byte-compiled",
0x450c0d0a: "python 3.1 byte-compiled",
0x4f0c0d0a: "python 3.1 byte-compiled",
0x580c0d0a: "python 3.2 byte-compiled",
0x620c0d0a: "python 3.2 byte-compiled",
0x6c0c0d0a: "python 3.2 byte-compiled",
0x760c0d0a: "python 3.3 byte-compiled",
0x800c0d0a: "python 3.3 byte-compiled",
0x8a0c0d0a: "python 3.3 byte-compiled",
0x940c0d0a: "python 3.3 byte-compiled",
0x9e0c0d0a: "python 3.3 byte-compiled",
0xb20c0d0a: "python 3.4 byte-compiled",
0xbc0c0d0a: "python 3.4 byte-compiled",
0xc60c0d0a: "python 3.4 byte-compiled",
0xd00c0d0a: "python 3.4 byte-compiled",
0xda0c0d0a: "python 3.4 byte-compiled",
0xe40c0d0a: "python 3.4 byte-compiled",
0xee0c0d0a: "python 3.4 byte-compiled",
0xf80c0d0a: "python 3.5.1- byte-compiled",
0x020d0d0a: "python 3.5.1- byte-compiled",
0x0c0d0d0a: "python 3.5.1- byte-compiled",
0x160d0d0a: "python 3.5.1- byte-compiled",
0x170d0d0a: "python 3.5.2+ byte-compiled",
0x200d0d0a: "python 3.6 byte-compiled",
0x210d0d0a: "python 3.6 byte-compiled",
0x2a0d0d0a: "python 3.6 byte-compiled",
0x2b0d0d0a: "python 3.6 byte-compiled",
0x2c0d0d0a: "python 3.6 byte-compiled",
0x2d0d0d0a: "python 3.6 byte-compiled",
0x2f0d0d0a: "python 3.6 byte-compiled",
0x300d0d0a: "python 3.6 byte-compiled",
0x310d0d0a: "python 3.6 byte-compiled",
0x320d0d0a: "python 3.6 byte-compiled",
0x330d0d0a: "python 3.6 byte-compiled",
0x3e0d0d0a: "python 3.7 byte-compiled",
0x3f0d0d0a: "python 3.7 byte-compiled",
0x400d0d0a: "python 3.7 byte-compiled",
0x410d0d0a: "python 3.7 byte-compiled",
0x420d0d0a: "python 3.7 byte-compiled",
0x480d0d0a: "python 3.8 byte-compiled",
0x490d0d0a: "python 3.8 byte-compiled",
0x520d0d0a: "python 3.8 byte-compiled",
0x530d0d0a: "python 3.8 byte-compiled",
0x540d0d0a: "python 3.8 byte-compiled",
0x550d0d0a: "python 3.8 byte-compiled",
0x5c0d0d0a: "python 3.9 byte-compiled",
0x5d0d0d0a: "python 3.9 byte-compiled",
0x5e0d0d0a: "python 3.9 byte-compiled",
0x5f0d0d0a: "python 3.9 byte-compiled",
0x600d0d0a: "python 3.9 byte-compiled",
0x610d0d0a: "python 3.9 byte-compiled",
}
def read_magic_numbers(file_path):
with open(file_path, 'r') as file:
lines = file.readlines()
results = []
flag = ''
for line in lines:
hex_value = int(line.strip(), 16)
if hex_value in magic_number_versions:
results.append(f"Hex: {hex_value:0x}, Version: {magic_number_versions[hex_value]}")
flag += magic_number_versions[hex_value].split(' ')[1].split('.')[1]
else:
results.append(f"Hex: {hex_value:0x}, Version: Unknown")
return results,flag
magic_file_path = 'magic.txt'
magic_numbers,flag = read_magic_numbers(magic_file_path)
for magic in magic_numbers:
print(magic)
print(flag)
import libnum
flag = int(flag)
print(libnum.n2s(flag))
f = open('flags.zip','wb').write(libnum.n2s(flag))
zip里面是secret.txt,有密码,是伪加密,修改头的07为00,尾的09为00,得到
Please decrypt the flask-session, the password is weak.
Data:eyJhbGdvcml0aG0iOiJkZXMiLCJmbGFnIjoiVW5BbVBWWTRhdCt2bkJqellPNytUZEZSMmZEYnhScytqQzdsMWt2b2hUMFp4clBDOEJUTWJBPT0ifQ.ZkyTwA.KPlAnhfBH8qMClLyoP6yboafHyw
跑rockyou找到密码是12312312
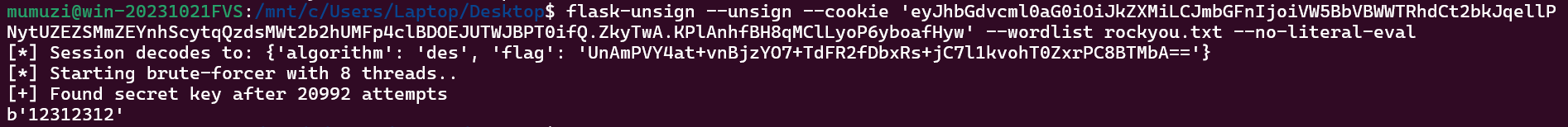
解DES就行
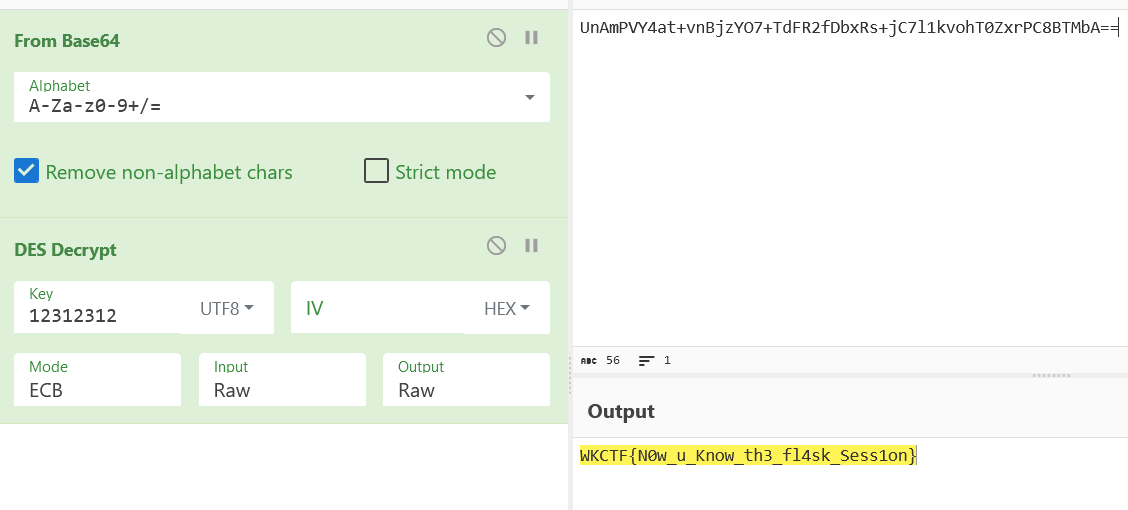
WKCTF{N0w_u_Know_th3_fl4sk_Sess1on}
**小z的社交网络
被迷惑了好久,除了躺门刚回来继续这看题就有想法了
实际上,虽然进行加密了,但是这里清一色的data都是相同的,直接可以不用考虑怎么解密,把整个当成RGB的data
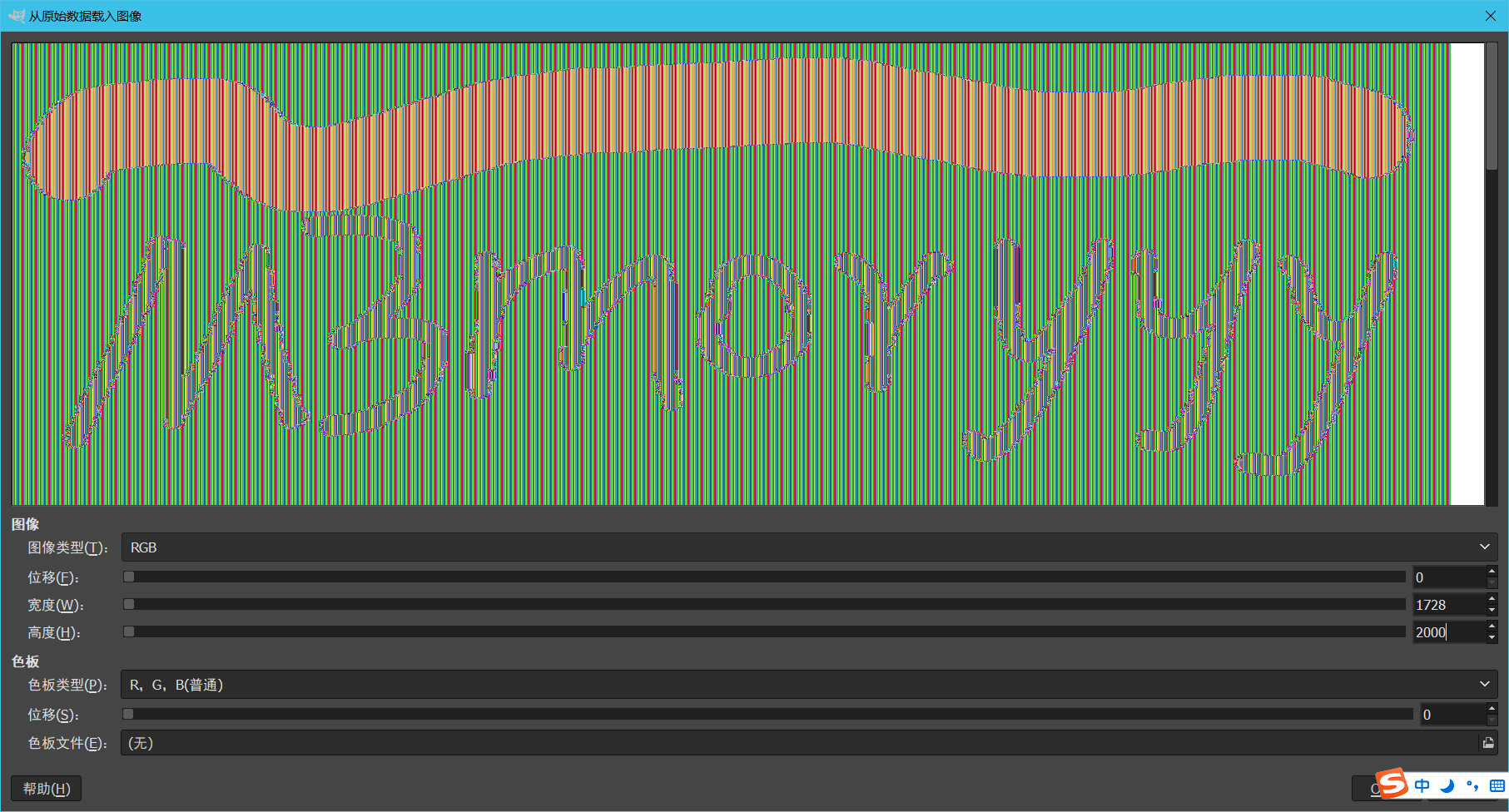

获得了IDM3moryyy,后面不知道,国内找了12个常见平台国外找了6个,没找到可疑的。
Web
有点无语,大家都可以传文件上去,然后没有做权限,tp的两个靶机都被别人搞坏了,就只能等着修
qiandao
flag在根目录,源代码提示用?file。http://110.40.35.73:15560/?file=file:///flag
不过为什么flag是WFCTF
WFCTF{Do_You_1ike_WkCTF_have_FUunN}
ez_tp
题目被有心之人玩坏了,题目直接变成qiandao题了,打发跟之前一样。
预期应该是thinkphp6.0.12的RCE或者反序列化吧,当时做的时候https://blog.csdn.net/m0_71518346/article/details/128360317能写东西但我执行不了写入后的文件,反正还在做的时候靶机就被404了。