OSCTF2024
2024-7-13 14:00——19:30
好几个月没怎么做题了,闲着无聊做做,能做多少做多少吧,说真的平台卡的要死
然后看了看最近DK盾又更了几个类型服务器,湖北高防(游戏云、云服)(主力节点)、香港CN2、成都高防(封udp)
截止发WP的时候,传家宝系列还有6台,配置4C8G,只能说是血赚不亏(续费同价):DK盾云服务器
然后也可以加入官方QQ群,经常有抽奖活动(比如7月13又抽20台洛杉矶云),群号727077055
Misc
Weird Video
直接记事本打开
OSCTF{T3xt_3DiT0r_FTW!}
Cyber Quiz
纯你问我答,可以第一次先随便输入把全部问题拿到,然后一块问GPT
答案分别是:
80
Tim Berners-Lee
Domain Name System
Encryption
HTTPS
Structured Query Language
SQL injection
Ransomware
Spoofing
certificate
Phishing
Firewall
DDOS
SMTP
Virtual Private Network
[不知道,RCE不对]
patch
Multi-Factor Authentication
nmap
SFTP
Cross-Site Scripting
拿到OSCTF{L33t_Kn0w_3Dg3},组词发现后面的单词是knowledge,因此后面那个下划线应该是l,得到flag
OSCTF{L33t_Kn0wl3Dg3}
Find the Flag
在首页查看源代码搜索OSCTF{得到flag
OSCTF{D1d_y0u_F1nd_m3?!}
Cryptic Pigeon
密文ᒷ1ᒣ☐0⟓ᒣ0⊔🝕🝕🝕🝕,猪圈(变体,码表ABCDEFGHINOPQRSTUVJKLMWXYZ)
明文P1GE0NG0BRRRR
flag为
OSCTF{P1GE0NG0BRRRR}
Finding the Seed
经典题目,进服务器算种子
不过这个题给了command.txt
Step 1: /register <password> <password> OR /login <password> (If already registered)
Step 2: Click survival NPC
Step 3: /warp seedcracker
Step 4: /redeem OSCTFACCESS
Step 5: Crack the seed.
不过我还是在本地装了seedcrackerX和Wurst,方便计算以及开桂
然后最简单的方法:到海边找5个沉船
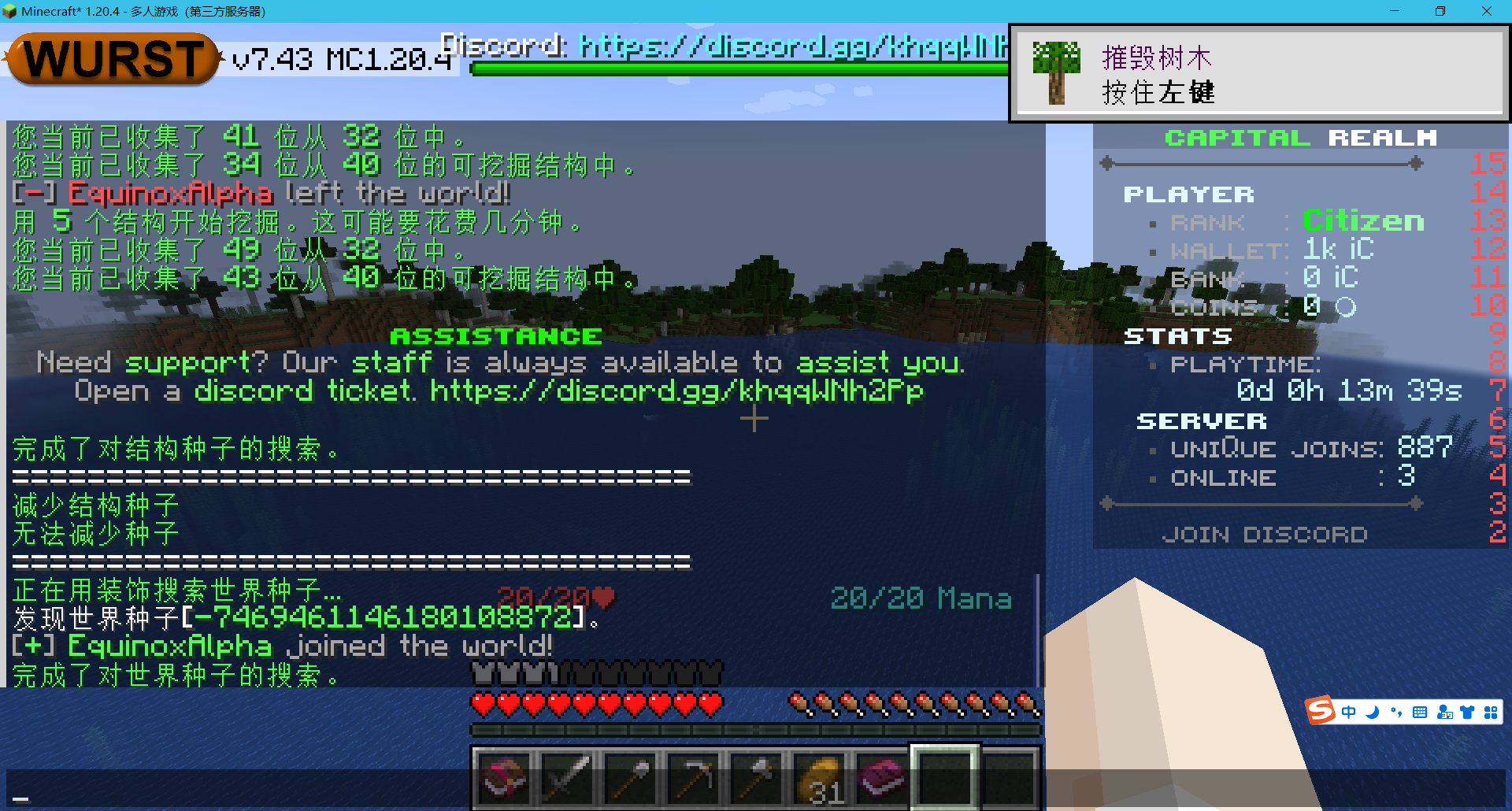
OSCTF{-7469461146180108872}
BF
过check然后base92
原始字符串=tFd>Q7_/Of$=![MJUtai{]m4{SD,'+!CQsxlS2ggV^ZiI%2-]2g
flag是
OSCTF{Bf_M34ns_BruT3_F4rc3_W1tH_L0V3!!!!!}
Code Breaker
服务器依旧是刚刚的Seed服务器,只不过要求提交的是:
NOTE: If you find the code use /osctf WXYZ where W,X,Y,Z represent +ve natural number to get the flag!
进去了之后发现是8个拉杆,但是设置了权限,无法拉下
这里开自由视角的时候发现后面的情况
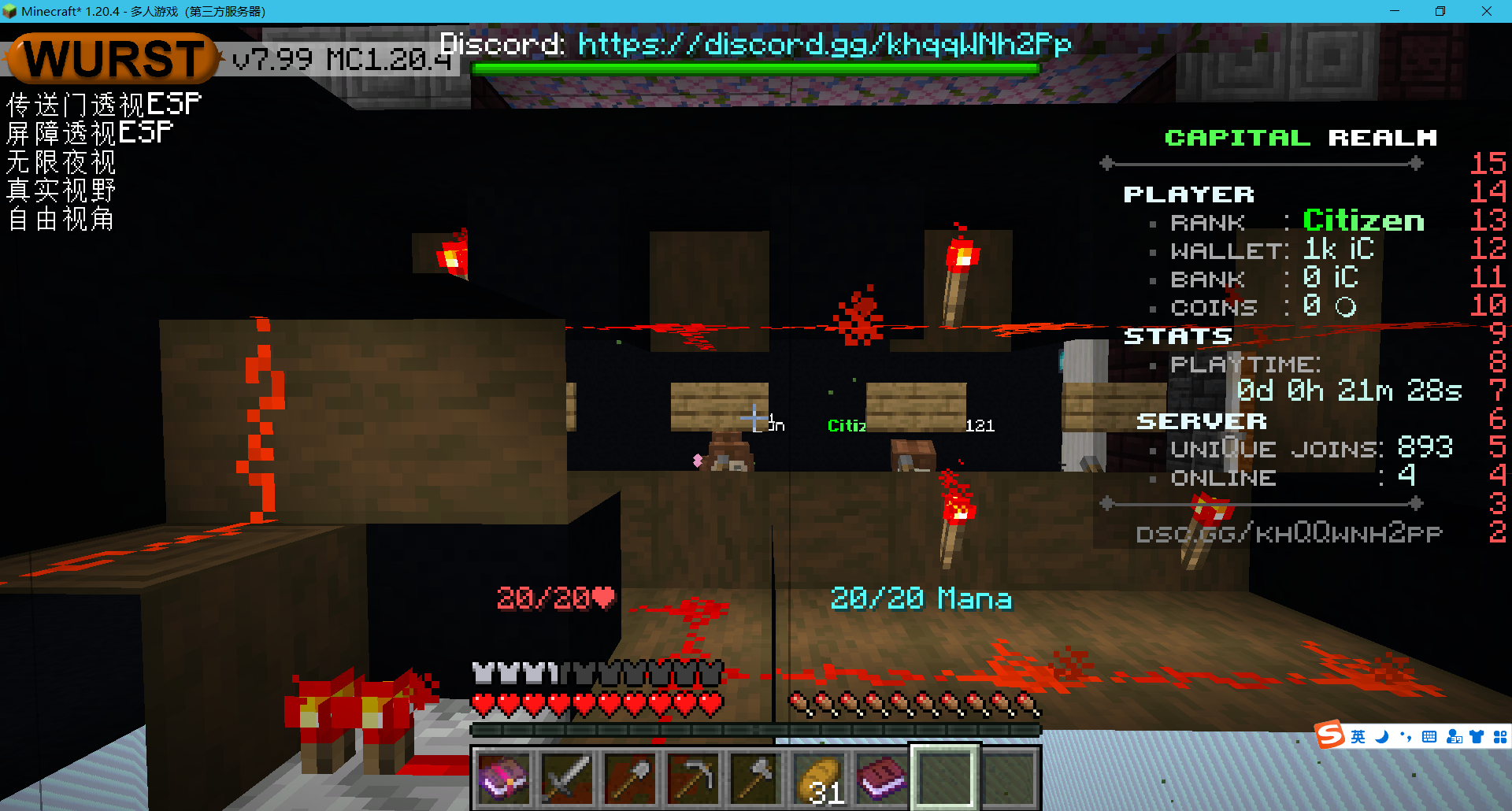
猜测想问的是,拉下哪4个拉杆可以触发,这里对应2456,输入/osctf 2456
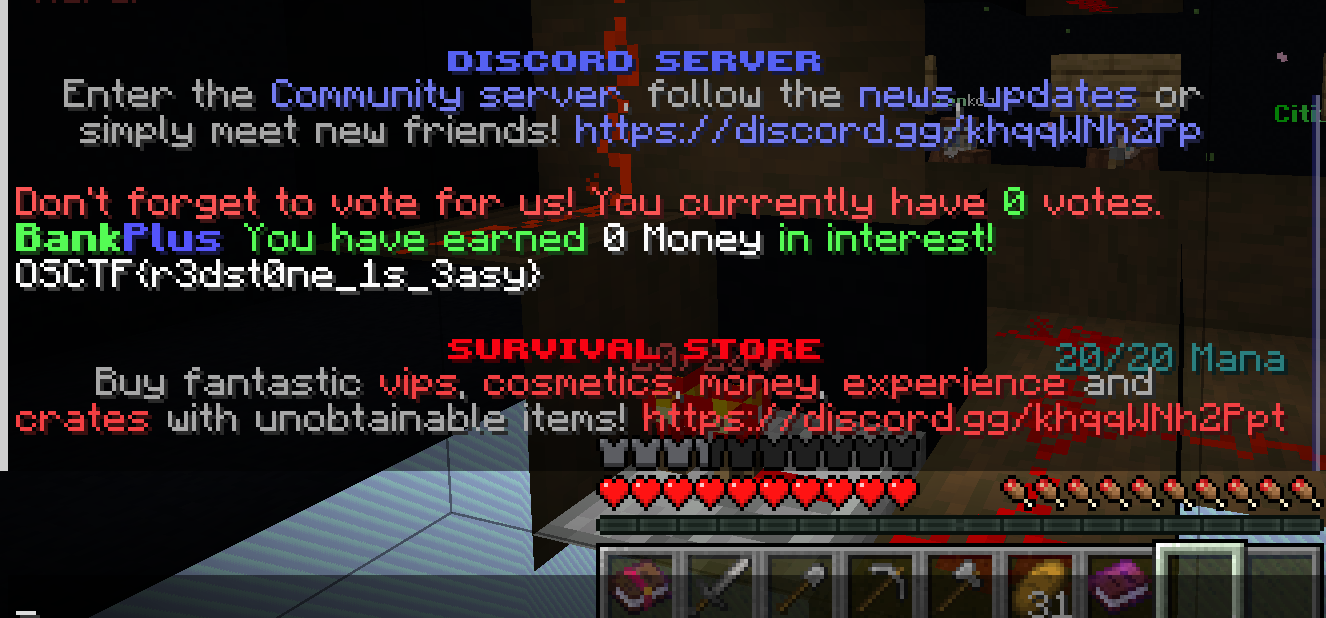
OSCTF{r3dst0ne_1s_3asy}
Binary Chaos
这里尝试了很多,最后发现是binaryfuck
def binaryfuck_to_brainfuck(binary_code):
bf_mapping = {
'000': '+',
'001': '-',
'010': '>',
'011': '<',
'100': '.',
'101': ',',
'110': '[',
'111': ']'
}
commands = [binary_code[i:i + 3] for i in range(0, len(binary_code), 3)]
brainfuck_code = ''.join(bf_mapping[cmd] for cmd in commands if cmd in bf_mapping)
return brainfuck_code
binary_code = open("message .txt",'r').read()
brainfuck_code = binaryfuck_to_brainfuck(binary_code)
print(brainfuck_code)
得到的结果拿去解密,得到的内容是这样的:
pythonflag_chars = ['B', '4', '{', 'c', 'F', '}', '_', 'K', 'n', 'F', 'T', 'O', 'S', '1', 'C', 'r', '#', 'y']
indices = [11, 14, 5, 8,L4,L17,L10,L9Xx13,x4,x3,x0,x1,x12,x2,x15,x7,x16]defassemble_flag chars¤ÄidxsÍ:×ííííðToúDoreturn*44MmPrintmthemassembledmflagwprint(assemble_flag(flag_chars, indices))w
然后需要基于索引中的值来确定它们在最终字符串中的位置
去掉奇奇怪怪的符号之后,出现了两个4,缺少了一个6,按照OSCTF格式,能够知道最先出现的那个4其实是6
flag_chars = ['B', '4', '{', 'c', 'F', '}', '_', 'K', 'n', 'F', 'T', 'O', 'S', '1', 'C', 'r', '#', 'y']
indices = [11, 14, 5, 8, 6, 17, 10, 9, 13, 4, 3, 0, 1, 12, 2, 15, 7, 16]
sorted_flag = [''] * len(indices)
for idx, char_idx in enumerate(indices):
sorted_flag[char_idx] = flag_chars[idx]
final_flag = ''.join(sorted_flag)
print(final_flag)
**My Dear Friend!
discord题,能做多少做多少吧
首先进去在公告看见part5:}
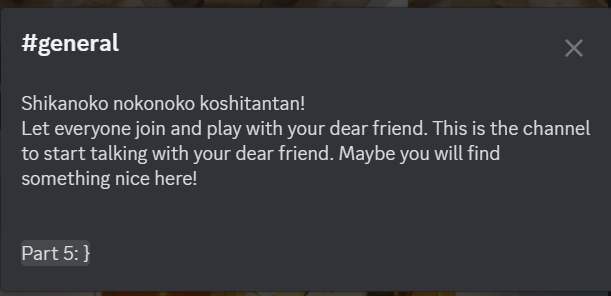
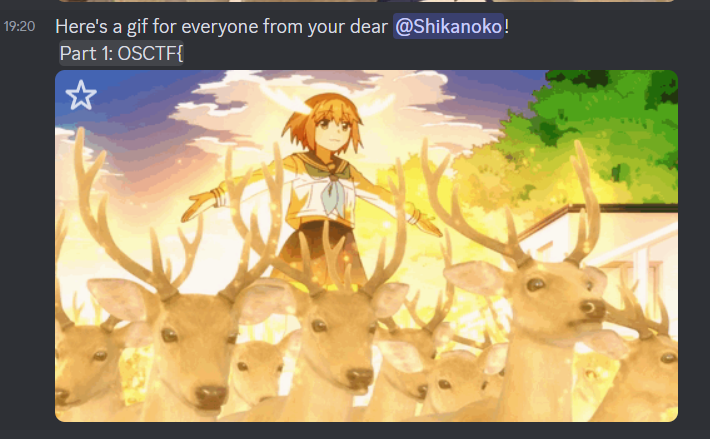
然后每分钟会发一条消息,包含了part1是OSCTF{
然后在机器人这里找到一个帮助:
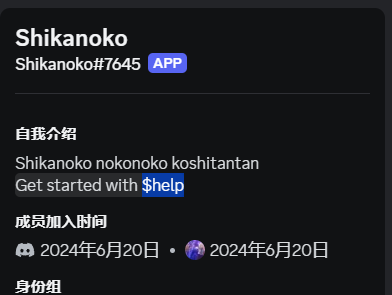
然后提示输入$chat创建私人对话,私人对话里面又有新的功能
$help: show this message
$gif: send a gif
$secret: send the secret (if you have permission)
$msg: send a message to shikanoko
这里尝试发gif,就是part1,发送msg只是提醒收到了消息,发送secret显示不能查看
因此这里尝试发送了$msg $secret,得到一句话:Your dear friend don't have any [text](https://part2.sh1k4n0k0_/) secret for you to show off!
因此得到part2是sh1k4n0k0_
然后发现在私聊的聊天公告里面,有一段part4:K0sH1T4nT4n
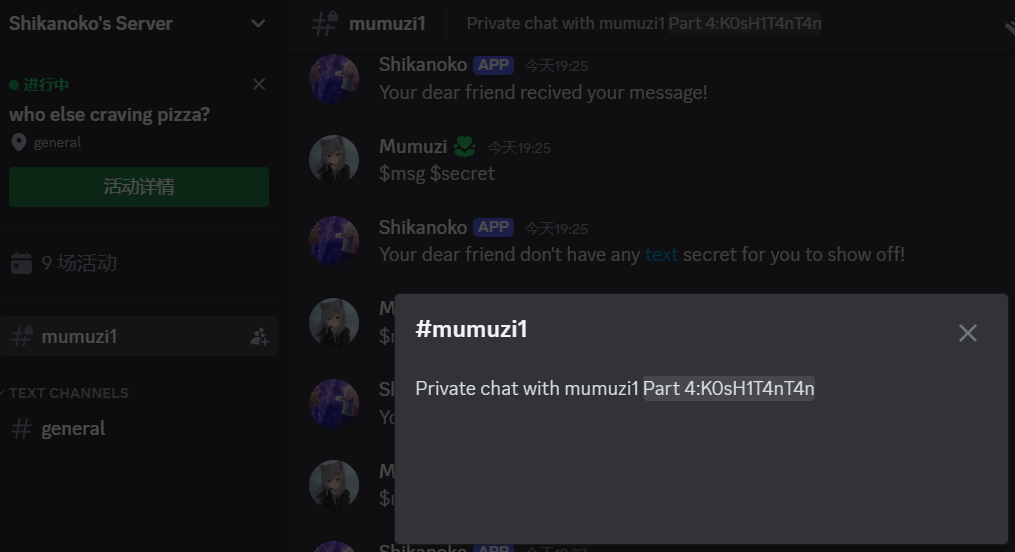
那么现在就差一段part3
Forensics
The Lost Image Mystery
文件尾FF D9,那么就是要修文件头,在IF前面补上FF D8 FF E0 00 10 4A 46,然后就能正常打开看见flag
OSCTF{W0ah_F1l3_h34D3r5}
The Hidden Soundwave
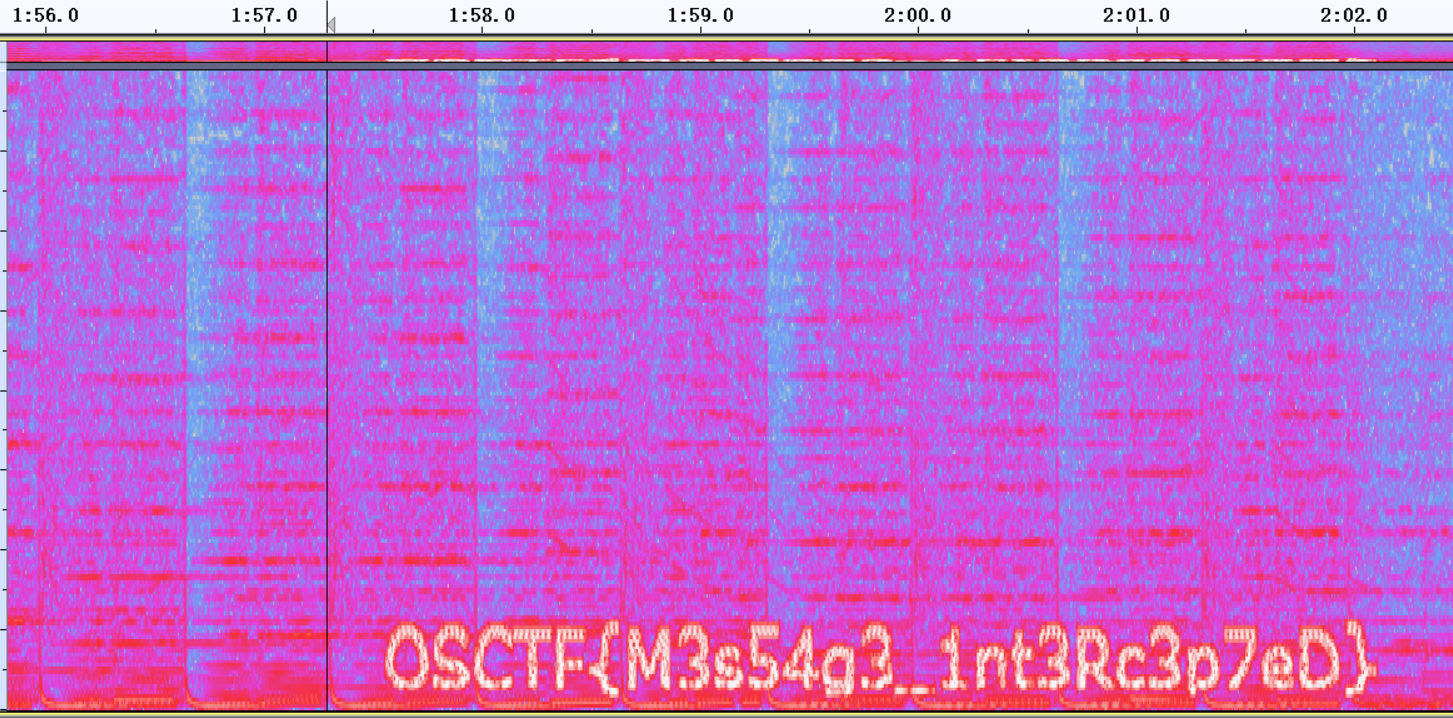
OSCTF{M3s54g3_1nt3Rc3p7eD}
PDF Puzzle
属性里面
OSCTF{H3il_M3taD4tA}
Seele Vellorei
把图片移开
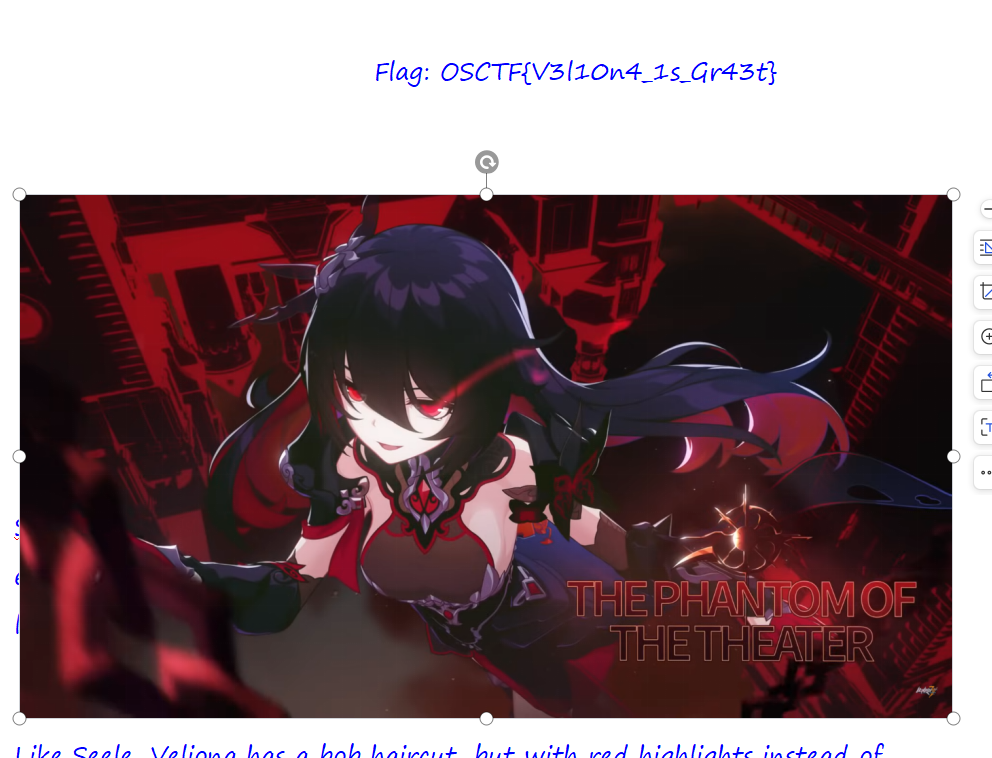
OSCTF{V3l10n4_1s_Gr43t}
Mysterious Website Incident
导进excel之后把间距正常拉开明显能看到一个链接,访问即flag
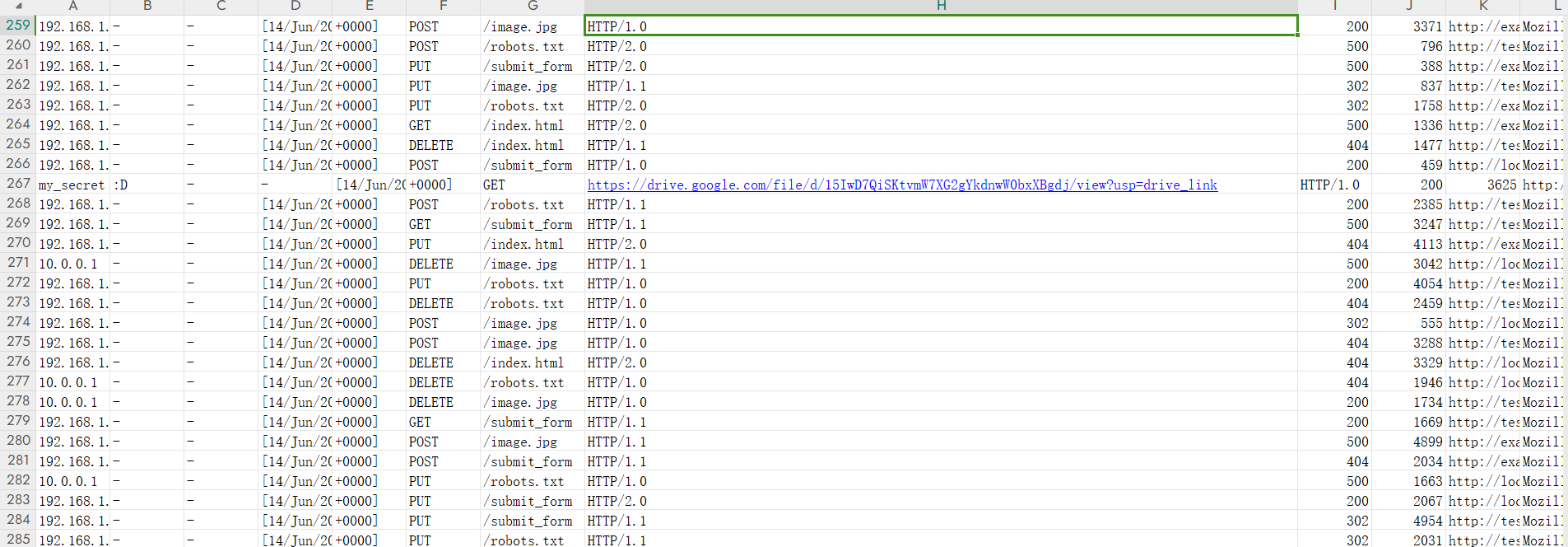
OSCTF{1_c4N_L0g!}
Phantom Script Intrusion
里面有个全局变量的值是\150\x58\x58\x70\x73\72\x2f\57\163\150\x30\162\164\x75\x72\x6c\56\x61\164\x2f\x73\x31\146\x57\62
转换后得到内容是https://shorturl.at/s1fW2,访问就是flag
OSCTF{M4lW4re_0bfU5CAt3d}
This is a QRCODE, but I can not scan it, whyyyyy????
就是遮��了定位点还有一少部分数据,手动补一下得到这个

OSCTF{r3c0vsR_qR_C0de?13_s0_fUn}
这里能发现第一个单词的e变成了s,对比3和s之后发现一个是00110011一个是01110011,那么读一下后面的13也能猜出来应该是1s,然后问号修改成下划线。尝试提交,正确
OSCTF{r3c0v3R_qR_C0de_1s_s0_fUn}
Cyber Heist Conspiracy
说是邮件,在下载的outlook files里找到Notifications.eml,把base64解一下就是一个压缩包,密码在正文里面是CreditsCardForFree
然后这个xlsm改成zip解压之后找xl文件夹就能看到显眼的vbaProject.bin
Crypto
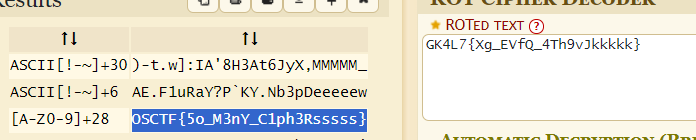
Cipher Conundrum
base64+hex+rot
The Secret Message
e = 3的RSA
import gmpy2
import binascii
n = 95529209895456302225704906479347847909957423713146975001566374739455122191404873517846348720717334832208112563199994182911677708320666162110219260456995238587348694937990770918797369279309985690765014929994818701603418084246649965352663500490541743609682236183632053755116058982739236349050530235419666436143
e = 3
c = 123455882152544968263105106204728561055927061837559618140477097078038573915018542652304779417958037315601542697001430243903815208295768006065618427997903855304186888710867473025125
i = 0
while True:
if gmpy2.iroot((c+i*n),3)[1] == True:
m = gmpy2.iroot((c+i*n),3)[0]
break
i += 1
print(binascii.unhexlify(hex(m)[2:]))
#OSCTF{Cub3_R00Ting_RSA!!}
OSCTF{Cub3_R00Ting_RSA!!}
Couple Primes
qp很近,能分解n,直接yafu
import gmpy2
import binascii
q = 141985506897231941308512923885300128905042311260138568794604206121080701727914934144982091139843178794485634682609841794924046596349428012470654095827271229332196334064446305896952838867217202135745989681311949561794583125471246401285687229433924674917884710139141784537370509554520561718028000388149962362867
p = 141985506897231941308512923885300128905042311260138568794604206121080701727914934144982091139843178794485634682609841794924046596349428012470654095827271229332196334064446305896952838867217202135745989681311949561794583125471246401285687229433924674917884710139141784537370509554520561718028000388149962362681
n = 20159884168863899177128175715030429666461733285660170664255048579116265087763268748333820860913271674586980839088092697230336179818435879126554509868570255414201418619851045615744211750178240471758695923469393333600480843090831767416937814471973060610730578620506577745372347777922355677932755542699210313287595362584505135967456855068550375989801913361017083952090117041405458626488736811460716474071561590513778196334141517893224697977911862004615690183334216587398645213023148750443295007000911541566340284156527080509545145423451091853688188705902833261507474200445477515893168405730493924172626222872760780966427
c = 18440162368010249375653348677429595229051180035668845001125855048750591059785630865891877031796050869136099359028540172514890273415892550857190509410541828375948243175466417949548148007390803680005616875833010137407850955608659023797782656930905693262770473679394796595557898347900786445803645539553815614140428316398058138450937721961593146082399553119578102712100359284788650328835784603011091312735813903241087475279011862693938914825685547337081335030237385061397899718079346063519325222861490101383929790275635381333028091769118083102339908694751574572782030287570280071809896532329742115422479473386147281509394
e = 65537
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
m = gmpy2.powmod(c,d,n)
print(binascii.unhexlify(hex(m)[2:]))
#OSCTF{m4y_7h3_pR1m3_10v3_34cH_07h3r?}
OSCTF{m4y_7h3_pR1m3_10v3_34cH_07h3r?}
Efficient RSA
N太小了,能直接分解
import gmpy2
import binascii
q = 3058290486427196148217508840815579
p = 4289583456856434512648292419762447
n = 13118792276839518668140934709605545144220967849048660605948916761813
c = 8124539402402728939748410245171419973083725701687225219471449051618
e = 65537
phi = (p-1)*(q-1)
d = gmpy2.invert(e,phi)
m = gmpy2.powmod(c,d,n)
print(binascii.unhexlify(hex(m)[2:]))
#OSCTF{F4ct0r1Ng_F0r_L1f3}
OSCTF{F4ct0r1Ng_F0r_L1f3}
Web
Introspection
源代码看js文件即可
OSCTF{Cr4zY_In5P3c71On}
Style Query Listing...?
万能密码登录,把admin' or 1=1--+作为账号,123作为密码,进去之后show得到
OSCTF{This_is_a_fake_flag}
然后我发现可以直接访问/profile,试了一下/admin结果就是真的flag,看来正确解法是扫!
OSCTF{D1r3ct0RY_BrU7t1nG_4nD_SQL}
reversing
Avengers Assemble
第一个和第二个输入值的和等于 0xdeadbeef。
第一个输入值小于等于 0x6f56df65。
第二个输入值等于 0x6f56df8d。
第二个输入值与第三个输入值异或结果等于 2103609845。
b = 0x6f56df8d
sums = 0xdeadbeef
xors = 2103609845
a = sums - b
c = b ^ xors
print(f"OSCTF{{{a}_{b}_{c}}}")
OSCTF{1867964258_1867964301_305419896}
Gophers Language
用GO写的字符串比较,直接明文字符串
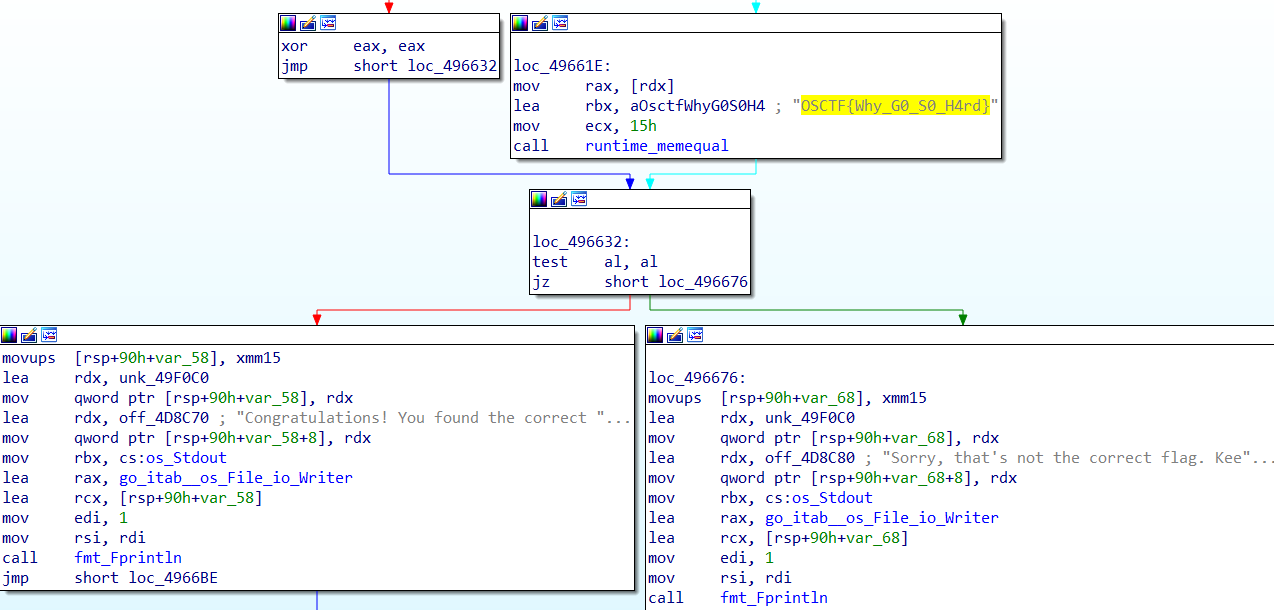
OSCTF{Why_G0_S0_H4rd}
Another Python Game
pyinstxtravtor逆exe然后uncompyle6逆pyc
# uncompyle6 version 3.9.0
# Python bytecode version base 3.8.0 (3413)
# Decompiled from: Python 2.7.18 (default, Oct 15 2023, 16:43:11)
# [GCC 11.4.0]
# Embedded file name: source.py
import pygame, sys
pygame.init()
screen_width = 800
screen_height = 600
screen = pygame.display.set_mode((screen_width, screen_height))
pygame.display.set_caption('CTF Challenge')
BLACK = (0, 0, 0)
WHITE = (255, 255, 255)
RED = (255, 0, 0)
BLUE = (0, 0, 255)
font = pygame.font.Font(None, 74)
small_font = pygame.font.Font(None, 36)
flag_hidden = True
flag_text = "OSCTF{1_5W3ar_I_D1dn'7_BruT3f0rc3}"
hidden_combination = ["'up'", "'up'", "'down'", "'down'", "'left'", "'right'", "'left'", "'right'"]
input_combination = []
player_size = 50
player_pos = [screen_width // 2, screen_height // 2]
player_color = BLUE
player_speed = 5
background_image = pygame.image.load('background.png')
background_image = pygame.transform.scale(background_image, (screen_width, screen_height))
def show_message(text, font, color, pos):
message = font.render(text, True, color)
screen.blit(message, pos)
running = True
while running:
for event in pygame.event.get():
if event.type == pygame.QUIT:
pygame.quit()
sys.exit()
elif event.type == pygame.KEYDOWN:
if event.key == pygame.K_UP:
input_combination.append('up')
else:
if event.key == pygame.K_DOWN:
input_combination.append('down')
else:
if event.key == pygame.K_LEFT:
input_combination.append('left')
else:
if event.key == pygame.K_RIGHT:
input_combination.append('right')
else:
if input_combination == hidden_combination:
flag_hidden = False
if len(input_combination) > len(hidden_combination):
input_combination.clear()
keys = pygame.key.get_pressed()
if keys[pygame.K_LEFT]:
player_pos[0] -= player_speed
if keys[pygame.K_RIGHT]:
player_pos[0] += player_speed
if keys[pygame.K_UP]:
player_pos[1] -= player_speed
if keys[pygame.K_DOWN]:
player_pos[1] += player_speed
player_pos[0] = max(0, min(player_pos[0], screen_width - player_size))
player_pos[1] = max(0, min(player_pos[1], screen_height - player_size))
screen.blit(background_image, (0, 0))
if flag_hidden:
show_message('Find the hidden combination to reveal the flag!', small_font, WHITE, (50,
50))
else:
show_message(flag_text, small_font, WHITE, (0, 0))
pygame.draw.rect(screen, player_color, (*player_pos, player_size, player_size))
pygame.display.flip()
pygame.time.Clock().tick(30)
# okay decompiling source.pyc
OSCTF{1_5W3ar_I_D1dn'7_BruT3f0rc3}